As modern technology advances, more bad-faith actors are finding new ways to get around the latest security features.
One of the new attacks is a multi-factor authentication (MFA) fatigue attack, a strategy which is used to gain access to an account through the new MFA technologies that are widely available.
However, if you know what to look for, you can easily protect yourself from attacks like these. In this article, we’re going to go over the ins and outs of the MFA fatigue attack, and how you can protect yourself today.
What is an MFA Fatigue Attack?
A multi-factor authentication (MFA) fatigue attack is an attack to attempt to circumvent the MFA security features that are built into most modern applications.
Also known as MFA bombing, the attack is a social engineering attack where attackers constantly push MFA authentication requests to the victim. The aim of this is to force the victim to accept the notification — and therefore gain access to the platform.
This attack is used after having acquired the password for the target account, which can be done using other social engineering attacks. Usually, the attack will lead to data exfiltration or a malware attack, such as ransomware, which will take your business’s data hostage until a ransom is paid.
How Does an MFA Fatigue Attack Start?
Compromise Credentials (previous hacks/reuse of password)
For an MFA fatigue attack to work, the credentials of an account have to be initially compromised. This is usually done through social engineering attacks or through a previous breach of a third party.
At this point, it’s assumed that the attacker already has the credentials. After all, you can’t start an MFA fatigue attack without already having password access to the account.
Use Stolen Credentials to Send MFA Push Notifications
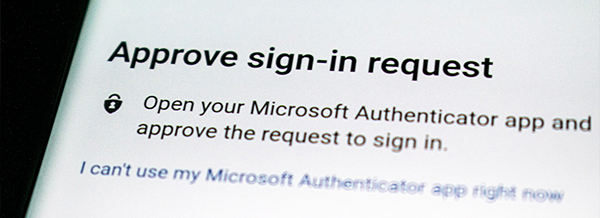
Essentially, the attacker will send MFA push notifications constantly to the victim’s devices. These prompts will essentially ping on said devices, which will be a hassle for the victim anyway.
A lot of these push notifications will have a simple ‘Yes’ button to click, while some platforms have more complex authentication options.
Victim Clicks Yes Eventually
Eventually, the goal is to have the victim click yes to give access to the account — after getting frustrated with the number of MFA notifications they’re receiving.
This is why MFA fatigue attacks are known as social engineering attacks. They’re not hacks or anything super technical and instead, rely on human nature and the victim making an error.
Once the victim clicks yes on their device, the attacker will have complete access to the account that they’re trying to access utilising the attack — making the attack a complete success.
How to Combat MFA Fatigue Attacks
Use OTP-Based MFA
Rather than utilising MFA that uses the ‘Is this you?’ and ‘Yes/No’ systems, utilising OTP-based MFA will be an extra barrier between possibly allowing attackers in and not.
A one-time password (OTP) will be sent to your device to be entered within the login portal that you’re using. This will naturally mean that the attacker will need to gain the OTP from you, making this attack far less effective.
Single-handedly, this is the best way to stop MFA fatigue attacks — the OTP-based MFA methods all make MFA fatigue attack useless.
Use Conditional Access
Utilising a tool such as Azure Active Directory, you can utilise conditional access to ensure that your organisation can only be accessed on certain devices as well as with certain login methods.
This means that you can easily control which devices are able to have unfiltered access to your organisation’s most sensitive areas. This is great as it ensures that anyone trying to access your organisation from an external device will just get blocked from being able to do so.
Improve User Education
As with any social engineering attack, increasing awareness of it is a great way to warn people of the danger of this attack. By ensuring that everyone in your organisation knows what an MFA fatigue attack is, there’s a far lower chance that it will happen to anyone within your company.
This should be a basic part of any cybersecurity or security training, as it’s essential for everyone within your organisation. Therefore, make sure people know of the risks that they’re facing and the potential attacks that they can face.
Improve Password Hygiene
The catalyst for an MFA fatigue attack is having access to the first factor of authentication, which is usually the password for the account. By ensuring that attackers can’t access those details, you cut off the risk at its root.
Enforcing good password hygiene and educating on password hygiene is important for this. This includes complexity, repeating passwords, and ensuring that the passwords used aren’t reused passwords from other platforms — that could possibly have become breached.
Enforce Least Privilege Access
The principle of least privilege is a concept that maintains that a user should only have access to the specific data and resources needed to undertake a task. This means only giving access based on the specific task at hand, which reduces the amount of risk to your organisation.
By implementing this concept within your organisation, you ensure that sensitive parts of your organisation’s data only go out to those who need it.
How We Can Help
MFA fatigue attacks can be worrying for any organisation. With the sheer number of cyber threats to keep track of, such an easy form of social engineering is easy to overlook. However, by implementing these changes and educating your organisation, you ensure that everyone throughout your institution is protected.
If you’re looking to take further steps to protect your organisation from the wide range of attacks that you could be facing, get in touch with us today! We’re here to help, and to ensure that your institution is safe from any malicious attempts and bad-faith actors looking to damage it.Contact us now and see how we can help!
